Introduction
This article aims to present a comprehensive overview of the current landscape of the modularity development in the Blockchain ecosystem. It then continues to explore a leading protocol in the area: Celestia.
Monolithic Blockchains
During the first years of Blockchain development, networks focused on addressing all capabilities required to make it fully perform, from execution, to consensus and block creation. This type of approach is referenced as a Monolithic Blockchain, in which all infrastructure is held under the same network. Although this has been the industry standard so far, having Bitcoin and Ethereum networks as the two most prominent protocols, modular blockchains are rapidly growing in popularity,
How Monolithic Blockchains Work
Typically, a blockchain can be understood through the following steps:
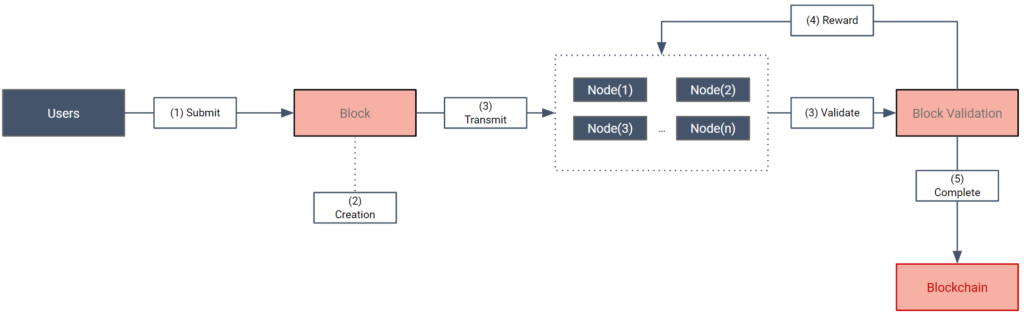
- Transaction Submission: Individuals interact with the network in a decentralized manner, exchanging assets using encoded private and public keys.
- Block Creation: The relevant information regarding this transaction is stored in a new block
- Information transmission: Info is then transmitted across all peer-to-peer computers contributing to the network.
- Block Validation: Through a specific consensus mechanism, a node is selected to perform the validation, ensuring all computers agree on the new state of the blockchain.
- Rewards: After the block’s hash value is authenticated and properly linked to previous ones, the validator receives a reward for the work provided, ensuring the right economic incentives for the network.
- Transaction Completion: Once the block is validated and all nodes agree, the transaction history is permanently stored on the blockchain network and users are properly rewarded.
Conceptual Layers
In order for this operation to be fully carried out and meet the standard criteria of being an immutable ledger, the network needs some conceptual layers to be defined and cooperate together.
- Data Availability Layer: This layer ensures that transaction data is accessible for the entire network to view. Once a transaction is finalized, the nodes should store a copy of it, and this data must be retrievable by every other operator in the network.
- Consensus Layer: This is the mechanism by which validators reach agreement on the block added to the chain. Proof of Work and Proof of Stake are the two most commonly used ones.
- Settlement Layer: This layer handles transaction confirmation, ensuring that it is irreversible and correctly stored, and ensuring its finality.
- Execution Layer: This is where transactions are processed according to the network’s rules in order to update its state.
Under a monolithic environment, as mentioned previously, all of those steps and layers are processed under the same infrastructure. In certain conditions, though, by concentrating all steps under the same network, this type of design can lead to poor usability and throughput congestion.
Monolithic Restrictions
Nodes under a monolithic environment carry the responsibility of accomplishing all the end to end components of a blockchain, that is, executing consensus, ensuring data availability and validating transactions. This type of underlying architecture can lead to relevant advantages in terms of security and decentralization.
However, by overloading nodes with all the operations behind the blockchain network, efficient execution and scalability can be compromised. That’s where modularity steps in: An approach in which blockchain components can be split apart, envisioning an ecosystem of cheaper and faster transactions.
Modular Blockchains
The core idea behind a modular blockchain is centered around Layer specialization. By doing so, each interaction can be optimal under their own purpose, reducing work load presented on a monolithic approach.
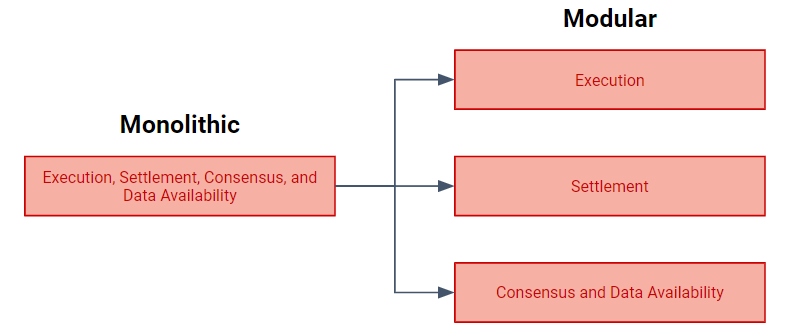
Decoupling the conceptual layers into individual applications enables greater flexibility and scalability within a system. Additionally, modularity allows different teams or third-party developers to contribute specialized applications that can seamlessly integrate with the overall architecture, opening up space for innovation in the industry that was not previously possible.
Modularity on Ethereum
As mentioned, Ethereum was natively built based on a monolithic approach. Even so, as the network increases its number of users, scalability and efficiency improvements are currently being constructed, so that throughput can grow proportionally. In other words, Ethereum itself is transitioning into a modular framework.
Sharding
Ethereum sharding is a modular approach in which functions can be split across multiple components. By separating the blockchain network into multiple shards, the system can achieve more output when compared to a model where all parts were carrying the same responsibilities.
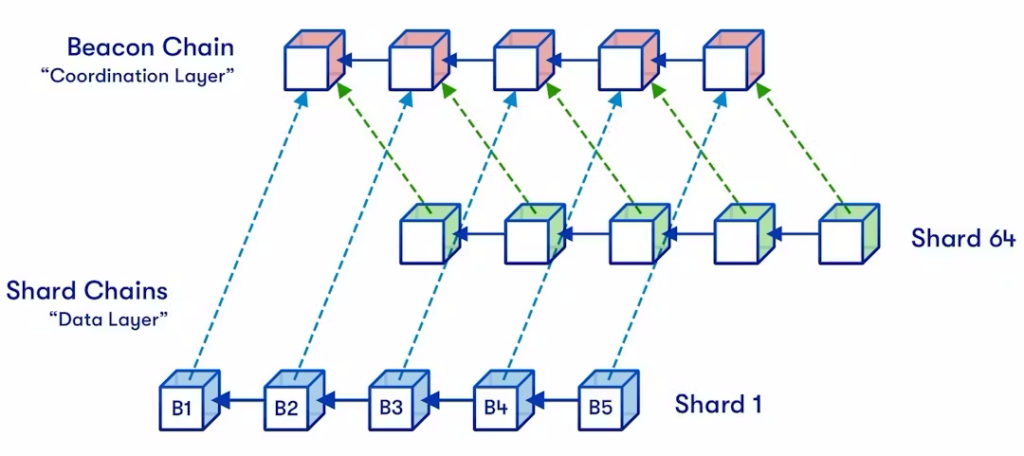
This approach allows for each shard to execute and store different pieces of the blockchain, being responsible only for the information contained in its own specific chain. Ultimately, this transition is an important milestone for Ethereum’s roadmap, as the chain will be able to onboard a larger number of transactions with segmented duties across the nodes.
Notably, some risks around sharding are also expected. Firstly, reducing the number of nodes per shard increases the probability of malicious activities, such as a 51% attack. Also, the codes being executed by smart contracts may become more complex, therefore subject to security vulnerabilities.
Rollups
Rollups are often regarded as one of the first and most relevant breakthroughs towards a modular blockchain stack. By leveraging Layer 1’s settlement, consensus, and data availability, execution is outsourced to off-chain nodes.
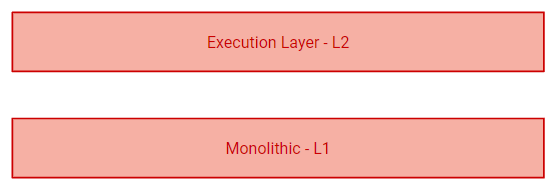
This modular approach has the potential to exponentially optimize throughout across a Layer 1, increasing block time and size without sacrificing underlying security. Ethereum has encompassed the rollup narrative into its roadmap, envisioning a future of cheap and secure transactions under a modular architecture.
Benefits
Scalability
By segmenting different layers, scalability can be achieved across blockchain projects as each piece of mechanism can be optimal on their own end. This represents a possible solution to the “blockchain” trilemma, which describes trade-offs between security, decentralization and scalability. on traditional blockchains. Modularity represents a huge milestone towards crypto mainstream adoption.
New Blockchains/Adaptability
Blockchain projects often face the difficult task of acquiring a base of validators for their networks, avoiding centralization and ensuring security. Modularity presents a new approach to this issue, as new projects can concentrate on specific tasks and delegate the security to an already established Layer 1. By doing so, builders can explore new approaches and solutions previously not viable to the community.
Drawbacks
Security
Different layers can’t guarantee security on their own, relying solely on the security chain chosen. if any problems happen in this chain, the project can be compromised.
Complexity
Modularity can add an extra layer of complexity when compared to monolithic blockchain. This factor can result in bugs or usability issues for new solutions created.
Token Value
By abstracting factors like security, the project’s native tokens might struggle to grow in utility, and therefore, long-term sustainability.
Celestia Case Study
Celestia is a modular data availability network, separating data availability from transaction execution.
Data Availability Problem
To better understand the work being done by Celestia, first it is necessary to address the “Data Availability Problem”.
Nodes Function
In a given blockchain, a block consists of two pieces:
- Block Header: Represents a meta-based type of information, consisting of basic information about it (ex: merkle roots)
- Transaction Data: Actual transaction history being held inside of the block.
Also, there are usually two types of nodes:
- Full nodes: Entities that download and check every transaction validity
- Light clients: Download only the block header and assume transactions are valid
The Data Availability Problem refers to the need to prove that the data entering the blockchain is correct, but doing so without requiring all nodes to download all the data. Of course, all data must be available so that the blocks can be verified independently, but forcing all the nodes to hold this information will result in scalability barriers.
Celestia’s data availability layer
Celestia’s solution to the Data Availability Problem use is based around two main pieces: Data Availability Sampling (DAS) and Namespaced Merkle Trees (NMTs).
- DAS: allows light nodes to verify data without downloading the entire block
- NMTs: assures that execution and settlement layers on Celestia download only relevant information to them.
Data availability sampling (DAS)
Usually, each node downloads a small and random subset of data. Given that the samples can be successfully downloaded, it means, with arguably high confidence, that all data is available across the network.
This mechanism can be achieved by something called data erasure coding, responsible for expanding a given dataset with redundant information (by fitting a polynomial function over the data and evaluating that polynomial at additional points). That type of technique can be seen in people’s daily routine, for example, in CDs. The fact that a CD can be scratched and still manage to retrieve the correct data is due to erasure coding techniques.
From a blockchain perspective, if any piece of information is unavailable, half of the expanded data will be missing. How many data samples each node checks can be adjusted so that if more than half of the data is missing, it’s almost certain that someone will notice the missing pieces.
Celestia leverages this piece of technology to enable its DAS by using a 2-dimensional Reed-Solomon (based on polynomial arithmetic) to encode the block data.
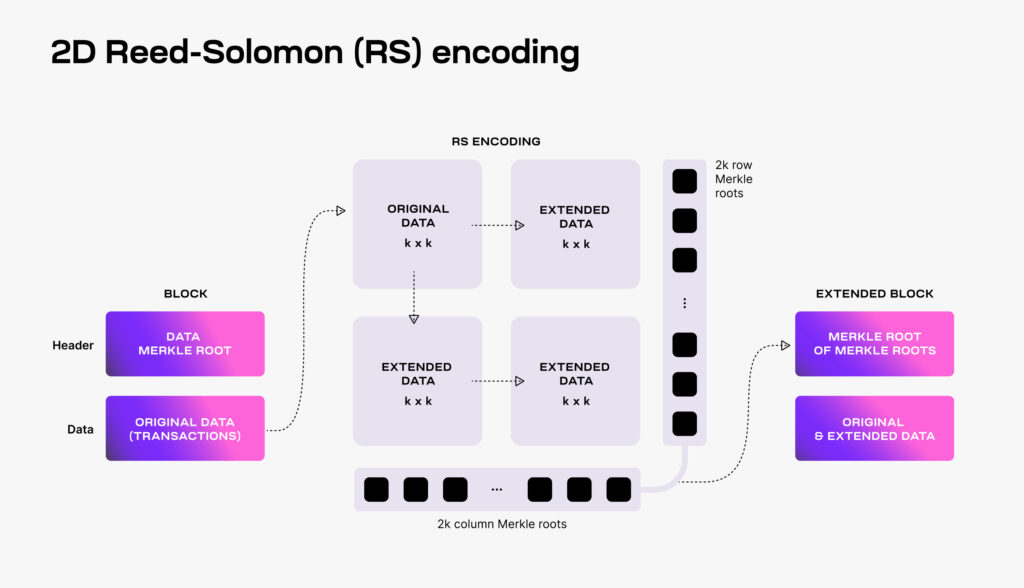
Image Source
The block data is split into k x k shares and then extended with parity data into a 2k x 2k matrix. So, for every row and column now containing the paraty values generated by the Reed-Solomon encoding, the new Merkle roots are computed. At last, a final Merkle root of all the conjoined Merkle root is generated and is used to add the block data commitment in the block header.
Path to Scalability
The increase in the number of light nodes allows more data to be collectively stored. Celestia nodes, however, still have to download the 4k intermediate Merkle roots. The protocol states that for a n^2 bytes, every node must download O(n) bytes. That is, for every light node entering the ecosystem, the throughput grows quadratically.
Fraud Proofs
Since Celestia does not have a mechanism to achieve consensus between block producers to guarantee data availability, malicious actors could compromise the network. The solution to that is the computation of Fraud Proofs, enabling light nodes to reject extended invalid data.
The need to download the 4k intermediate Merkle Root is necessary due a limitation of the standard Reed-Solomon encoding (1-dimentional), that could be used alternatively. Using a standard approach, all the original data would need to be downloaded (n^2) so that the nodes can reconstruct the data and submit proofs. On the other hand. 2-dimentional encoding relies only on O(n) bytes to verify only one row or one column of the extended matrix.
Namespaced Merkle trees (NMTs)
In order to ensure that an application using the DA layer downloads only the necessary information to its functioning, the layer must be able to prove the data is complete. An NMT is a modified version of a traditional Merkle tree where the leaf nodes are ordered by namespace identifiers, and the hash function is adjusted to incorporate information about the namespace ranges of all descendant nodes.
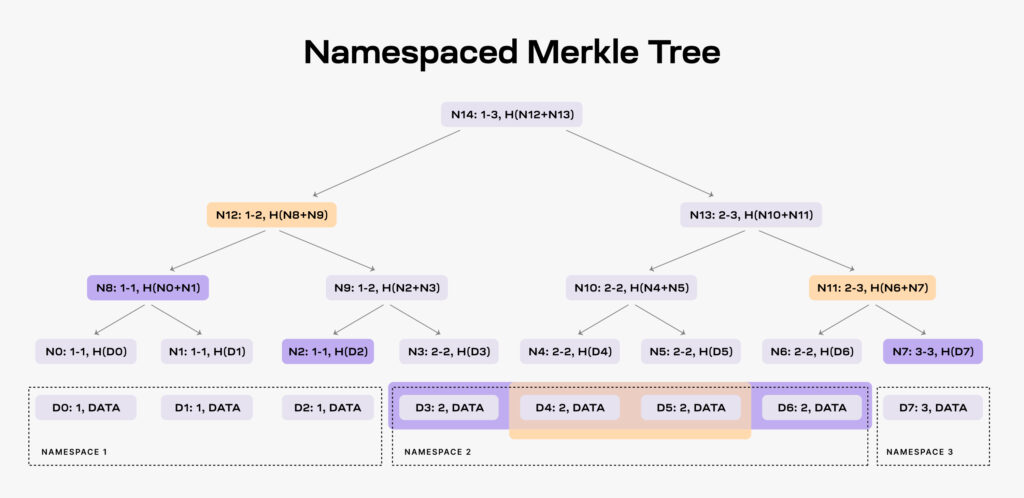
When an application requests data for a specific namespace, such as namespace 2, the DA layer must provide the requested data shares (D3, D4, D5, and D6) along with certain nodes from the NMT as proof (N2, N8, and N7). The application already possesses the root node (N14) obtained from the block header.
By providing these specific nodes as proof, the DA layer enables the application to verify two critical aspects:
- Data Authenticity: The application can verify that the provided data shares are indeed part of the block data, as they are backed by the Merkle root (N14) obtained from the block header.
- Data Completeness: Additionally, the application can ensure that all the data for the requested namespace (in this case, namespace 2) has been provided. This is done by examining the namespace ranges of the provided nodes. If the provided nodes cover all the data shares within the namespace range, the data is considered complete.
TIA Token and Economics
Celestia’s blockchain is powered by its native token named “TIA”. This section encompasses its main applications and economic behaviours.
Blobspace
Celestia users (rollup developers) have to pay to make their data available on the chain. All of these transactions must contain:
- identity of the sender
- Data to be made available
- Namespace
- Signature
This process is done by sending “PayForBlobs” transactions, charged with the TIA token. Celestia Block Producers (full nodes) hold the responsibility of batching multiple “PayForBlobs” transactions into one block (much like miners under a proof-of-work blockchain and validators in proof-of-stake blockchains), adding to the block header a commitment of the block data at the final step.
Rollup Creation
Besides paying for data availability, as it is currently done across Ethereum’s rollup development landscape, new rollups can leverage TIA tokens for gas under their chain.
PoS Rewards
Celestia allows for delegated proof-of-stake, which means users can delegate their tokens to a validator to gain a portion of the rewards.
The Blockchain framework being used is Cosmos SDK, counting with a validator set size of 100 validators, decided by active set ranking.
Governance
TIA provides governance power to tokens, enabling participation in crucial future decisions of the blockchain.
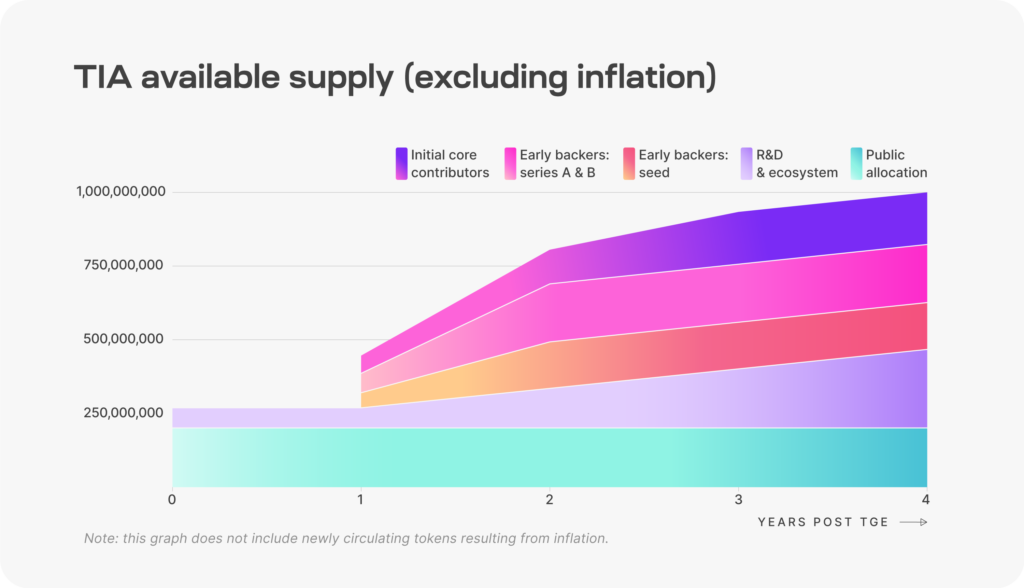
Inflation and Supply
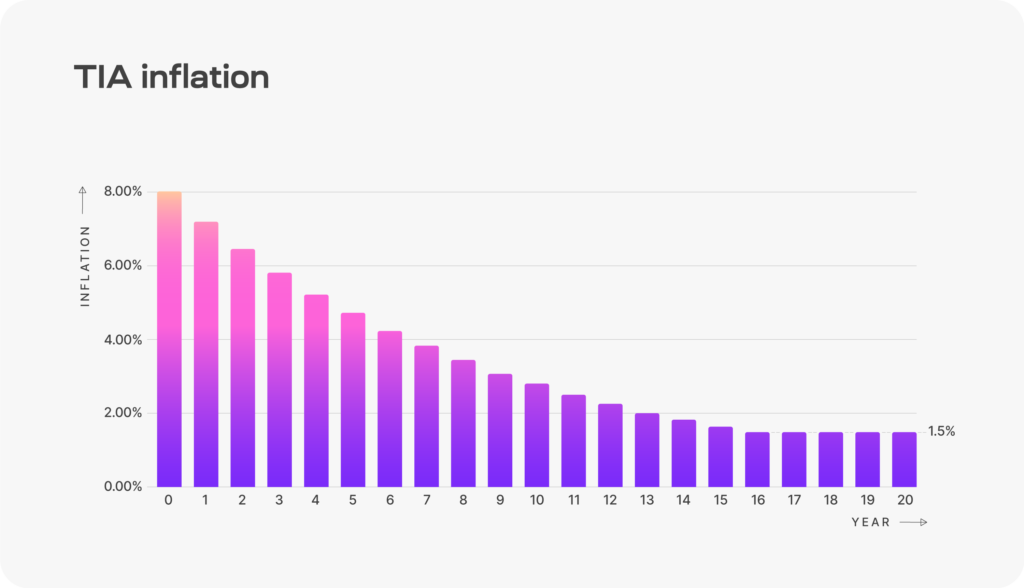
TIA inflation starts at 8% per year, decreasing 10% annually until it achieves 1,5%.
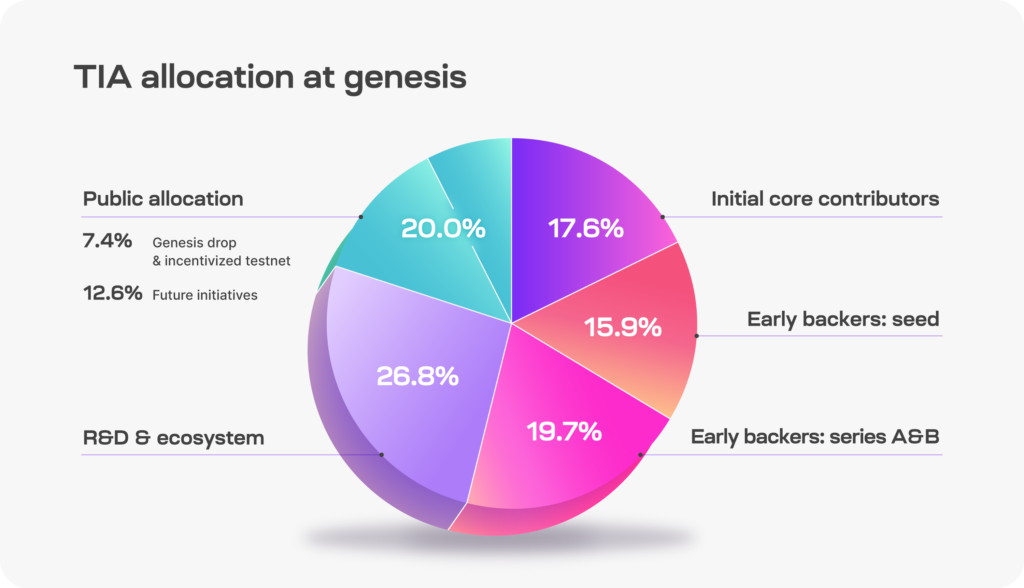
TIA’s total supply is 1.000.000.000 at genesis, split according to the picture:
This supply, however, is subject to unlocks over the years.
Long-term Sustainability
Celestia’s co-founder, Mustafa, stated that the network will achieve its sustainability through economy of scale:
”Celestia is a public good. Therefore, Celestia strives to achieve economic sustainability by providing high quality blockspace at scale to serve billions of people, rather than through artificial scarcity of resources. Resources should be priced to achieve economic sustainability, but not to be unnecessarily extractive.”
That being said, Celestia’s success is directly related to the network’s capacity to generate value and onboard a large number of users.
Types of nodes
Celestia has two separate networks – consensus and data availability. In each case, different types of nodes can provide their work:
Consensus:
- Validator node: participates in consensus.
- Full consensus node: sync blockchain history.
Data Availability:
- Bridge node: bridges blocks between the Data-Availability network and the Consensus network.
- Full storage node: stores all the data.
- Light node: conducts data availability sampling.
Each type of node will require different levels of storage capacity, as well as technical expertise to operate it properly.
Integration

Celestia allows seamless integration between different frameworks and tools.
By doing so, builders can customize their working blockchain framework to best fit their needs. The ultimate goal of modular blockchains is to make it as easy to deploy a blockchain as a smart contract. Some of the benefits of this approach are:
- No validator set is required.
- Security inheritance from the start
- Any part of the stack can be delegated
Risk Analysis
Celestia’s value proposition is solid, providing a viable and scalable solution to the data availability problem. As such, it is expected that a large number of builders will be interested in building on top of their blockchain. Analysing the protocol, however, some risk considerations must be discussed.
Nodes Incentives
In the current design, DA nodes are not incentivized to perform their work. Light nodes are the core players of the entire scalability theory behind the data availability layer, therefore, as the network continues to grow, it is necessary to make sure the number of DA nodes won’t become a potential bottleneck to the protocol’s adoption. Given the lack of incentives, as celestia reaches exponential adoption, that can configure a potential scenario in the future.
On that note, however, it is important to highlight that light nodes are used to pay for transaction publication on Celestia’s DA Layer, meaning that, the participation of the project itself creates new light nodes. Also, acting as an early adopter on the development of the network might reward users with future incentives.
TIA Token
Celestia’s token has some solid utility properties, as it is used both to power the transactions and staking rewards. It is important to take into account, though, its distribution in the following years.
In the next 4 years, as evidenced in the “TIA Token and Economics” section, TIA will achieve 1,000,000,000 billion units in circulation, on top of the programmed inflation. As of 22/07/2024, there are only 199,125,720 in circulation. In other words, Celestia has to grow in adoption quite significantly so that token holders won’t suffer from dilution.
Competitors
Modularity is an evolving landscape in which new solutions are being built every day. As stated by one of the founders, Celestia’s sustainability is attached to an economy of scale, meaning that, at the present moment, there won’t be an induced type of scarcity for the token. Celestia’s vision, then, is based on an ongoing process of acquiring users.
As competition continues to grow, Celestia might naturally lose some market share over the years, potentially compromising scaling the number of users. In this case, it is important to work on their retention and growth, differentiating its offerings from competitors, and ensuring that an economy of scale can be achieved.
In Conclusion
The modularity development in the blockchain ecosystem represents a significant evolution from the traditional monolithic approach, promising enhanced scalability, adaptability, and efficiency. By examining Celestia as a leading example of a modular blockchain, we see how it addresses the critical Data Availability Problem through innovative techniques like Data Availability Sampling and Namespaced Merkle Trees. The economic structure and utility of Celestia’s native token, TIA, along with its approach to scalability and security, position it as a strong contender in the modular blockchain space.
Article Researched and Written by :
Marcos Batalheiro
Marcos’ LinkedIn – https://www.linkedin.com/in/marcosposse/
References
https://www.bankless.com/2024-is-the-year-of-modular-expansion
https://usa.visa.com/solutions/crypto/monolithic-vs-modular-blockchain.html
https://www.alchemy.com/overviews/modular-vs-monolithic-blockchains
